The solution is simple to wipe in Windows 10 / 8.1 without third-party tools to clearing free space and prevent recovery of files and folders!If you don't want use third-party tools, like the freeware ... BlankAndSecure to prevent recovery of files and folders in Windows 8.1 or 10. 1.) ... Deleting with cipher!
|
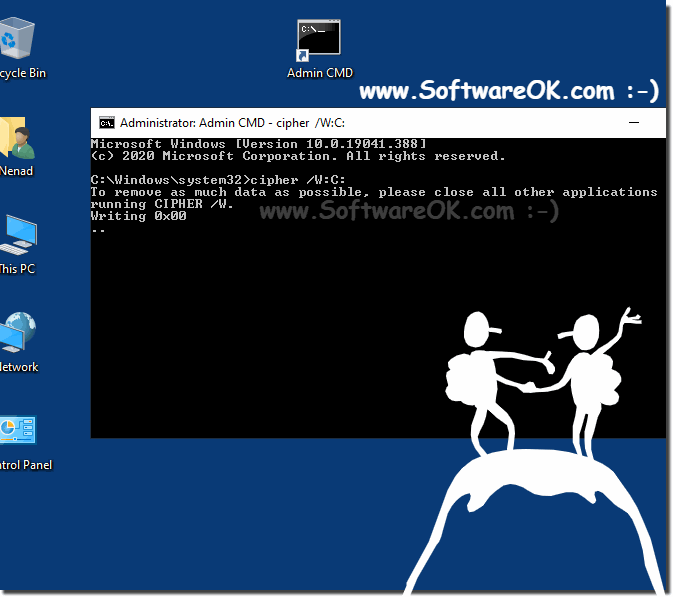
| (Image-1) Prevent recovery of files and folders in Windows 8.1 or 8 |
 |
When you delete files or folders on Windows 8.1, the file and folder data is not initially removed from the hard disk. Instead, the space on the disk that was occupied by the deleted data is "deallocated."
After it is deallocated, the space is available for use when new data is written to the disk. Until the space is overwritten, it is possible to recover the deleted data by using a low-level disk editor or data-recovery software.
2.) he command cipher and possibilities under Windows 11, 10, 8.1!
lllllllllllllllllllllllllllMicrosoft Windows [Version 10.0.19041.329]
(c) 2020 Microsoft Corporation. All rights reserved.
C:\Users\Nenad>cipher /?
Displays or alters the encryption of directories [files] on NTFS partitions.
CIPHER [/E | /D | /C]
[/S:directory] [/B] [/H] [pathname [...]]
CIPHER /K [/ECC:256|384|521]
CIPHER /R:filename [/SMARTCARD] [/ECC:256|384|521]
CIPHER /P:filename.cer
CIPHER /U [/N]
CIPHER /W:directory
CIPHER /X[:efsfile] [filename]
CIPHER /Y
CIPHER /ADDUSER [/CERTHASH:hash | /CERTFILE:filename | /USER:username]
[/S:directory] [/B] [/H] [pathname [...]]
CIPHER /FLUSHCACHE [/SERVER:servername]
CIPHER /REMOVEUSER /CERTHASH:hash
[/S:directory] [/B] [/H] [pathname [...]]
CIPHER /REKEY [pathname [...]]
/B Abort if an error is encountered. By default, CIPHER continues
executing even if errors are encountered.
/C Displays information on the encrypted file.
/D Decrypts the specified files or directories.
/E Encrypts the specified files or directories. Directories will be
marked so that files added afterward will be encrypted. The
encrypted file could become decrypted when it is modified if the
parent directory is not encrypted. It is recommended that you
encrypt the file and the parent directory.
/H Displays files with the hidden or system attributes. These files
are omitted by default.
/K Creates a new certificate and key for use with EFS. If this
option is chosen, all the other options will be ignored.
Note: By default, /K creates a certificate and key that conform
to current group policy. If ECC is specified, a self-signed
certificate will be created with the supplied key size.
/N This option only works with /U. This will prevent keys being
updated. This is used to find all the encrypted files on the
local drives.
/R Generates an EFS recovery key and certificate, then writes them
to a .PFX file (containing certificate and private key) and a
.CER file (containing only the certificate). An administrator may
add the contents of the .CER to the EFS recovery policy to create
the recovery key for users, and import the .PFX to recover
individual files. If SMARTCARD is specified, then writes the
recovery key and certificate to a smart card. A .CER file is
generated (containing only the certificate). No .PFX file is
generated.
Note: By default, /R creates an 2048-bit RSA recovery key and
certificate. If ECC is specified, it must be followed by a
key size of 256, 384, or 521.
/P Creates a base64-encoded recovery-policy blob from the passed-in
certificate. This blob can be used to set DRA policy for
MDM deployments.
/S Performs the specified operation on the given directory and all
files and subdirectories within it.
/U Tries to touch all the encrypted files on local drives. This will
update user's file encryption key or recovery keys to the current
ones if they are changed. This option does not work with other
options except /N.
/W Removes data from available unused disk space on the entire
volume. If this option is chosen, all other options are ignored.
The directory specified can be anywhere in a local volume. If it
is a mount point or points to a directory in another volume, the
data on that volume will be removed.
/X Backup EFS certificate and keys into file filename. If efsfile is
provided, the current user's certificate(s) used to encrypt the
file will be backed up. Otherwise, the user's current EFS
certificate and keys will be backed up.
/Y Displays your current EFS certificate thumbprint on the local PC.
/ADDUSER Adds a user to the specified encrypted file(s). If CERTHASH is
provided, cipher will search for a certificate with this SHA1
hash. If CERTFILE is provided, cipher will extract the
certificate from the file. If USER is provided, cipher will
try to locate the user's certificate in Active Directory Domain
Services.
/FLUSHCACHE
Clears the calling user's EFS key cache on the specified server.
If servername is not provided, cipher clears the user's key cache
on the local machine.
/REKEY Updates the specified encrypted file(s) to use the configured
EFS current key.
/REMOVEUSER
Removes a user from the specified file(s). CERTHASH must be the
SHA1 hash of the certificate to remove.
directory A directory path.
filename A filename without extensions.
pathname Specifies a pattern, file or directory.
efsfile An encrypted file path.
Used without parameters, CIPHER displays the encryption state of the
current directory and any files it contains. You may use multiple directory
names and wildcards. You must put spaces between multiple parameters.
C:\Users\Nenad>cipher /?
Prevent Recovery of deleted files under Windows 11, 10 Pro, Enterprise, Home, Windows 8.1, Windows 8, Windows-Server 2019, 2016, 2012, Windows 7 Basic, Professional, Starter, Ultimate
In Windows 8.1 the Administrators can use Cipher.exe to encrypt and decrypt data on drives that use the NTFS file system and to view the encryption status of files and folders from a command prompt. An updated version of the Cipher tool has been released for Windows 2000, and is included with Windows XP. The updated version adds another security option.
This new option is the ability to overwrite data that you have deleted so that it cannot be recovered and accessed.
3.) Is deleting with Cipher safe under Windows?
Freeing up free space using the Cipher command in Windows is a common way to overwrite deleted files and leftover data to ensure that they cannot be recovered. However, the security of this method is relative and depends on various factors:
Effectiveness: The Cipher command overwrites the free space with zeros. This provides some protection against simple data recovery attempts. However, there are professional data recovery tools and methods that can also recover deleted data from overwritten storage space if the overwriting is not done thoroughly enough.
Multiple Overwrite: In safety-critical environments, it is recommended to overwrite the free space multiple times (e.g. 3-7 times) with random data to further minimize the chances of recovery. The encryption tool in Windows does not provide a direct option for multiple overwriting and therefore may not be sufficient in such cases.
Professional data recovery: Advanced data recovery tools and techniques, especially in forensic or security contexts, can even recover multiple overwritten data in certain circumstances. For maximum security, physical destruction of the hard drive or the use of special data erasure tools may be necessary.
Encryption: An even more secure method is to encrypt the entire drive. When you delete an encrypted drive, decryption prevents access to the data.
Overall, the Cipher command in Windows provides a basic way to securely overwrite free space, but security depends on the requirements and threat model. In security-critical or forensic situations, you should consider additional measures to ensure that your data cannot be recovered.
FAQ 173: Updated on: 31 October 2023 09:07
